Would you…
- Hire an employee, then do a background check?
- Buy a used car, then take it to a mechanic for inspection?
- Purchase a home, then hire a home inspector?
… of course not! A significant investment requires appropriate research. Why then would you do the same with your critical business information technology? Let us help you manage your cyber security and reduce the likelyhood of ransomware, malware, data loss, and much more.
What is Co-Managed Cyber Security?
Most small businesses don’t have the expertise, time, or tools to properly manage the cyber security of their enterprise, A Co-Managed Cyber Security solution leverages our expertise as the managed service (security) provider to implement those policies, processes, and people to make that a reality.
We bring our expertise to your table, and you bring your company culture, information technology and management style. Together, we can build a more secure enterprise.
Zero Trust Initiative
The prevailing IT mindset has always been “Trust, then verify”. Trust everything, and only block the bad content, applications, and websites. Using best-in-class tools and processes, DNS Enterprises will modify your IT methods to “Verify, then trust”. PC’s, networks, firewalls, data, applications, internet access – all can be made secure by design.
Risk Mitigation
When you have assets, there’s always risk to those assets. We help mitigate your IT risks by first identifying risks, then prioritizing them. After that, we can choose to:
- Avoid
- Mitigate
- Transfer
- Accept
Engaging with us
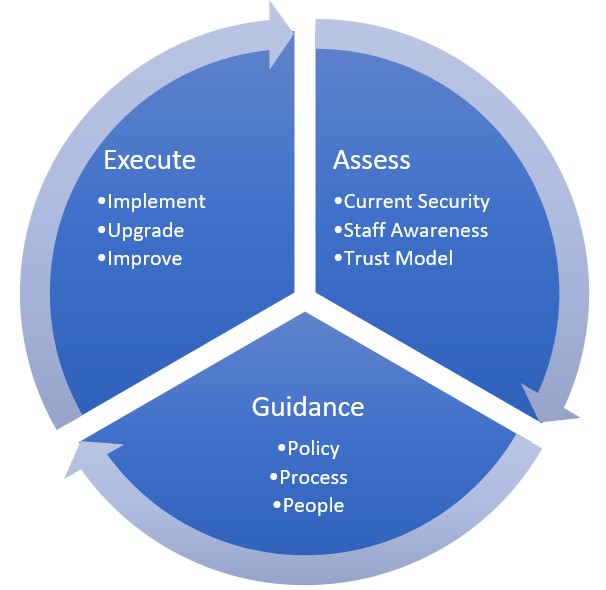
Our methodology is to first assess, guide and execute the improvements to your information technology. Depending on the enterprise requirements, this might require repeating the cycle for iterative improvements.
- Analyzing your current security stance
- Microsoft 365 Secure Score
- Ransomware Business Impact Analysis
- User Security Awareness Baseline
- Dark Web Scan
- Phishing Test
- Security Policy Review
- Firewall Rule Review
- External Penetration Test*
- Internal Security Audit*
- Active Directory Audit*
- Risk Analysis*
- Chart your path to improved security
- Recurring meetings to review policies, processes and people
- Define business roles and associated policies
- Implementation of appropriate Microsoft 365 Security recommendations
- Execute
- Implement
- Upgrade existing technology
- Improve processes
* These items are available for an additional fee
Contact us today to see how we can help improve your IT security!
