IT Security is Job #1
We are proud to state that none of our managed service clients have ever been ransomed while under our watch.
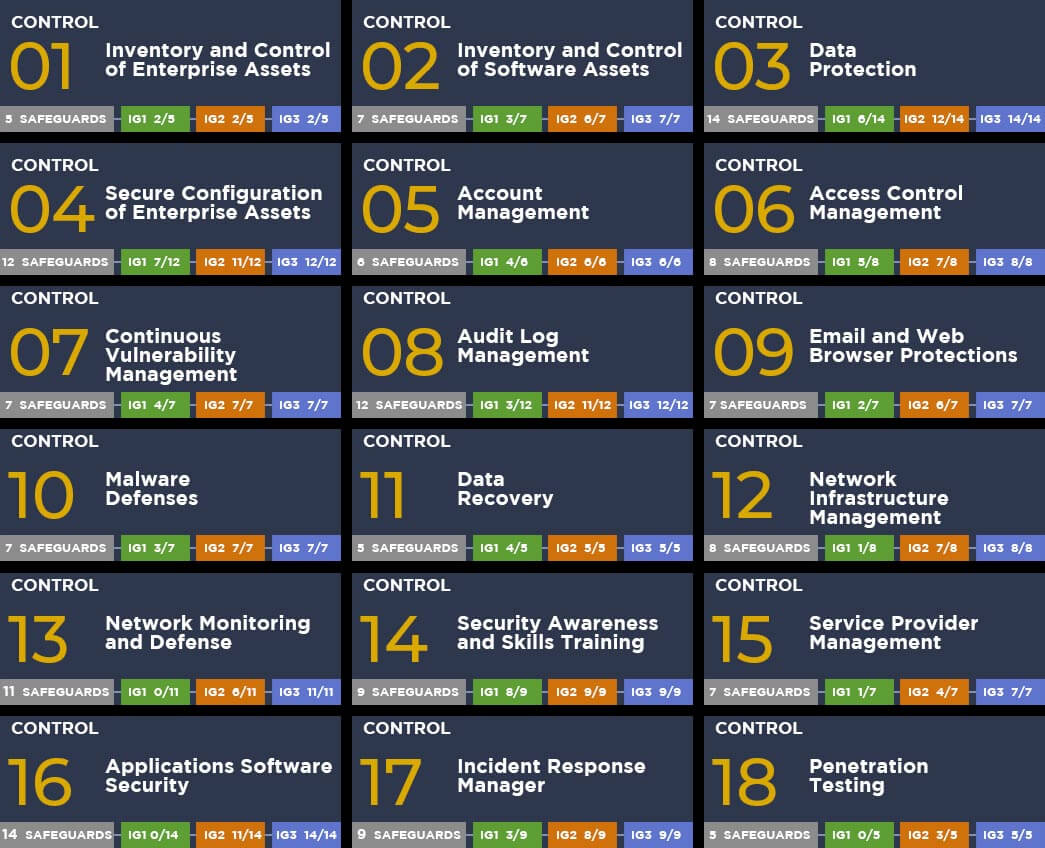
We will help and guide you in implementing Center for Internet Security “CIS Controls”, a set of IT standards globally recognized as foundational for business security and cyber hygiene.
Meet with us today to find out how we can help make your IT more secure and operationally mature.
What Our Clients Say
Follow DNS Enterprises on LinkedIn“Daryl is very knowledgeable and can solve our problems quickly the first time. He will be an asset to anyone who needs his service.”
Chris A.
General Manager
“Daryl rescued our wireless network from total disaster and has continued…”
Dr. Holly D.
CEO
“Daryl gets things done. An expert at networking, security and teaching, if you call him into your situation…Problem Solved.”
Marc C.
IT MANAGER
“One of the biggest benefits with Daryl is he always displayed a strong willingness to share knowledge with our internal staff.”
Craig W.
Information Security
“Daryl is a network demi-god that has more IT experience than many entire departments”
Keith P.
OWNER
In the fifteen (15) years I have known Daryl he has been an instructor, mentor, problem solver, and trusted adviser to me. Daryl personally helped me learn and progress through the IT and Information Security ranks, from hands-on technical certifications as a system engineer through strategic management credentials as a Chief Information Security Officer.
Rowley M.
direct, Cyber risk management
Latest News

FBI CJIS Certification… check!
The FBI’s Criminal Justice Information Services takes IT security seriously. We’re proud to have CJIS Security and Privacy Training Certification for another year running!
Read more
US immigration officials installed personal apps on work phones
ICE workers at US Customs get a major reprimand for installing personal, vulnerable and in some cases, banned, apps on company devices. This opens ICE up to attack! See US[…]
Read more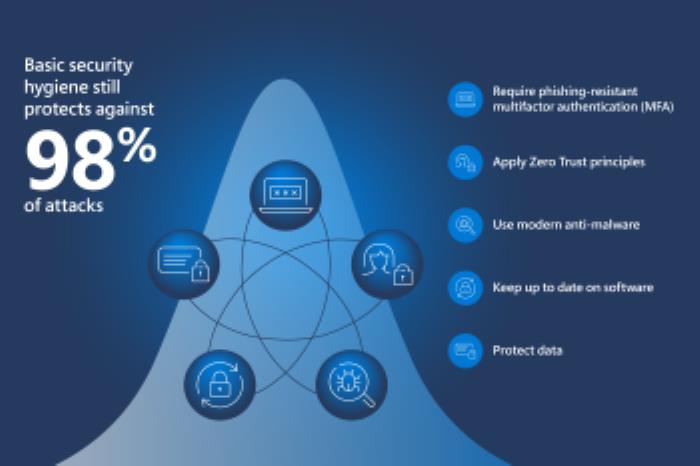
Microsoft Security Guidance
Microsoft put out a great article recently, Cyber Resilience Hygiene Guide | Security Insider (microsoft.com) Highly recommended if you are in either management or IT. While it does dive a[…]
Read more
